Identifying Viruses
Most people are uncertain when it comes to viruses. What exactly is a virus, and what is not? How can you tell if you have a virus or not, and what type do you have? What do viruses do? Why were they even created in the first place? This three part article should help you to answer these questions, and learn how to better deal with viruses.
Signs Of A Virus
There are many different signs of a virus. Below are listed some of the most common.
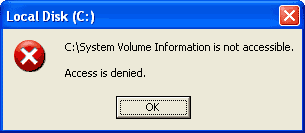
1) Restricted Access
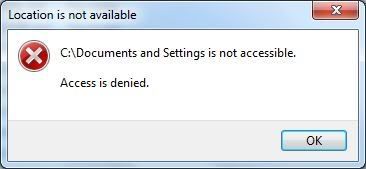
One surefire way to know there is a virus on your computer is if programs and normal operations start to go haywire. For example, if you try to go to a folder on your desktop, or "My Documents", and get an error message like these:
Another example is programs that usually work just fine will not start, and will show errors as to why they cannot start. If one of these programs is your virus protection not starting up and giving you an error when you start your computer, then chances are you have caught a virus.
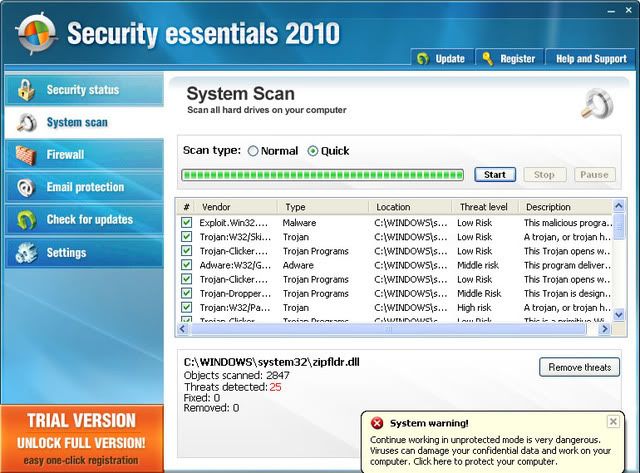
2) Malicious/Impostor Programs
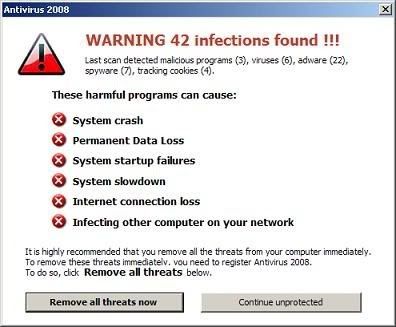
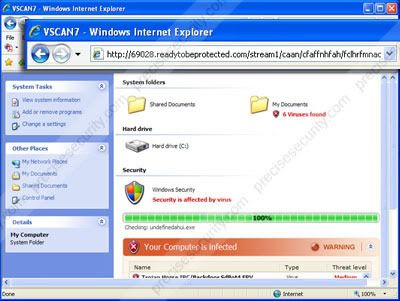
Another good way to tell you've got a virus is if an Anti-Virus program you have never seen before is showing up when you start your computer, saying you have a ton of viruses, and you need to purchase the full software to get them off. That program it's self is a virus, and a hoax used to scam people.
3) Excessive Pop-ups/ Web Browser Problems
If you get excessive pop-ups, and/or your browser is acting strange, or not working as it should, whether it is Internet Explorer, Mozilla Firefox, Google Chrome, etc., you likely have a virus. Especially if your homepage has been changed to something strange without your knowledge of having changed it. If opening your web browser causes your computer to freeze up, and/or crash, you definitely have a virus.
4) Strange Things Happening/Possessed Computer
You may notice your cursor moving on it's own, or your keyboard's lights flickering on and off on their own. Programs, folders, and other things may open on their own, and it might seem as if a ghost is using your computer, or it has been possessed. This is a sure sign that you have a nasty kind of virus. *Note: If you notice you have this problem, unplug your computer from the internet immediately.
5) Excessive Slowness
Sometimes excessive slowness is a result of a virus. This isn't always the case, however. If your computer is acting extremely slow, you should run a disk cleanup and defragmentation. If that doesn't fix the problem, it is possible you have a virus. [In which case, if you're in Central Florida, feel free to give us a call at 863-838-2663 !] If you're in any other area, you will want to contact a computer technician, and have them assess the system to find the cause of the slowness.
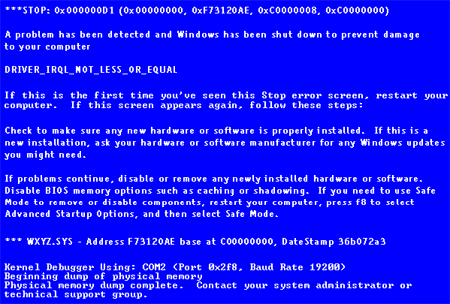
6) System Hang-Ups/Crashes, Fatal Errors, and Blue Screens
Often, system hang ups, fatal errors, blue screens, and crashing systems are caused either by viruses or the aftermath of one [you may have recently caught it with your antivirus, or had someone remove it for you]. If this is the case, run a virus scan, and if it comes up empty, you will want to give a computer technician a call, and have him look at it. [Again, if you're in the Central Florida area, nearby Lakeland, give us a call!]


 n
n