In this day and age, there are many things people need to keep their computer systems safe, secure, and optimized. In this article, we will go over a few very useful programs and tools you may want to look into if you do not already use them. [As well as a few fun programs that come in handy]
Note: All of the software in this article can be found online for free! Simply click on the image to go to the download page for the program, and more information about it.
Note: All of the software in this article can be found online for free! Simply click on the image to go to the download page for the program, and more information about it.
ANTI-VIRUS
Avast Anti-Virus
Avast is a free anti-virus software suite that is noted as one of the best on the internet today.
Avast puts all of their effort towards virus research, and online distribution. Avast comes with an active scanning system that monitors your downloads, internet browsing, e-mail attachments, and other key places for virus intrusion. It is one of the least system heavy virus protection programs out there, and gets the job done efficiently.
Microsoft Security Essentials
Microsoft Security Essentials is the latest [free] Virus Protection released from Microsoft. It is completely free, and is also very gentle on system resources. It does a great job with virus protection, and will find about anything. The main difference between Security Essentials and Avast is that Security Essentials does not have an active shield constantly monitoring certain aspects. It will usually catch incoming viruses through a web browser if you go to the wrong site on accident, or something of that nature, but it is always good to run a quick-scan with this scanner at least once a week. It is extremely fast though, and you will find next to no lag in your system while it is scanning.
CLEANUP
CCleaner
CCleaner is a freeware system optimization tool with a good amount of very useful features. If you're not familiar with the term "freeware", it means that it is completely free to use!
CCleaner can be used for a number of thing, but as it's title suggests, it's main intended purpose when it was created, was to cleanup your system; and it does it amazingly well. It can do an analysis to show you how much space it will free up. When you click analyze, it searches through temporary files, and unneeded files in Windows, Internet Explorer, Firefox, etc.
It also can scan intelligently for cookies, and will leave them on your system, so when deleting your temporary internet files you will still be logged into the sites you had left yourself logged into [ie. Facebook, Myspace, Twitter, etc.]
Another useful tool that it has is the Registry Cleanup tool. Fear not, those of you whom think this tool would tinker with your registry. It does not make any changes, it merely gets rid of unused file extensions, and other unused entries. [Sometimes when you uninstall a program, it leaves file extension types, and other unneeded junk in your registry.]
CCleaner also has a tool to uninstall programs [much like the Control Panel's add/remove programs, only this one tends to load faster], and also a tool to look through, and disable unwanted startup programs. If you're tired of seeing a certain program boot up each time you start your computer, and believe it is making it start up slower.
The company that makes this cleanup tool is known as Piriform, and they have a great number of other useful, and interesting tools. This tool in particular is great if your computer is running slow, or if you just feel you need to free up some unnecessary clutter.
File Reovery
Recuva
Accidentally deleted a file you really needed? Something important you think you may have lost due to self error? Fear no more! Recuva is a file recovery system from Piriform that can recover files that have been permanently deleted, or emptied from the recycle bin. While this may scare a lot of you, fear not; there are tools out there as well that can be used to make multiple passes over these deleted files, so this program cannot pick them up [CCleaner has one known as drive wiper, but there are also tools out there that can be used when deleting individual files].
Networking
Hamachi
[Also known as LogMeIn Hamahi²]
Hamachi is a very useful networking tool, used for setting up what would normally be a local network over the internet. If you install it and join a network, you can share files, network drives, etc. You can even have LAN parties with your friends; playing your favorite games together, without having to meet up and drag around your computer! It is as if you are on a local network, only there is no actual set up required. You simply install the software, set up your username, connect to the network you or a friend has created using the software, and you're in.
Hamahi uses some of the leading encryption and authentication in the industry, and is extremely secure, so you can rest easy, knowing that your information is safe.
Visual Effects
Object Dock
Tired of having so many desktop icons? Here's the solution!
Object Dock is small dock much like that on a Macintosh Operating System. It can stay at the bottom, top, right, or left side of your screen, and holds icons that when clicked will launch. [Much like the new taskbar in Windows 7]. You can customize it's appearance in many different ways, and can set it to autohide, or animate it; making it to where when you hover over it with your cursor, the icons zoom, or shake.
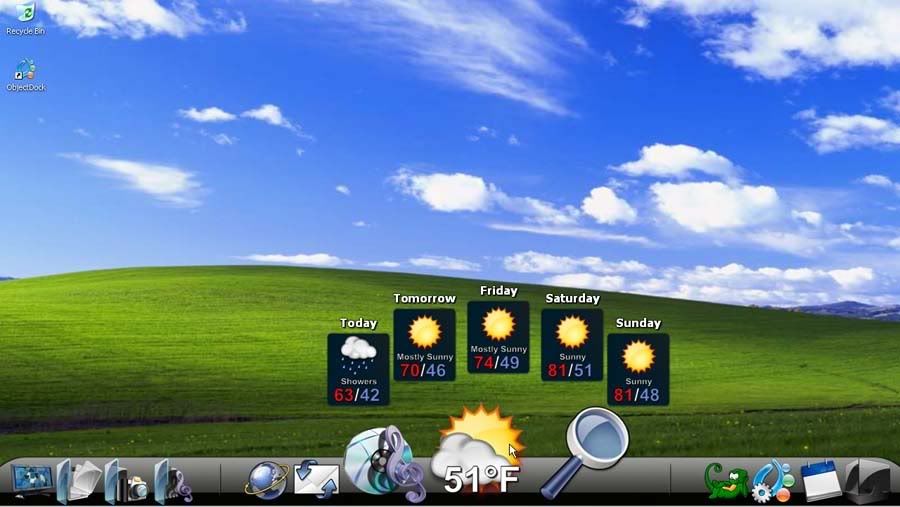
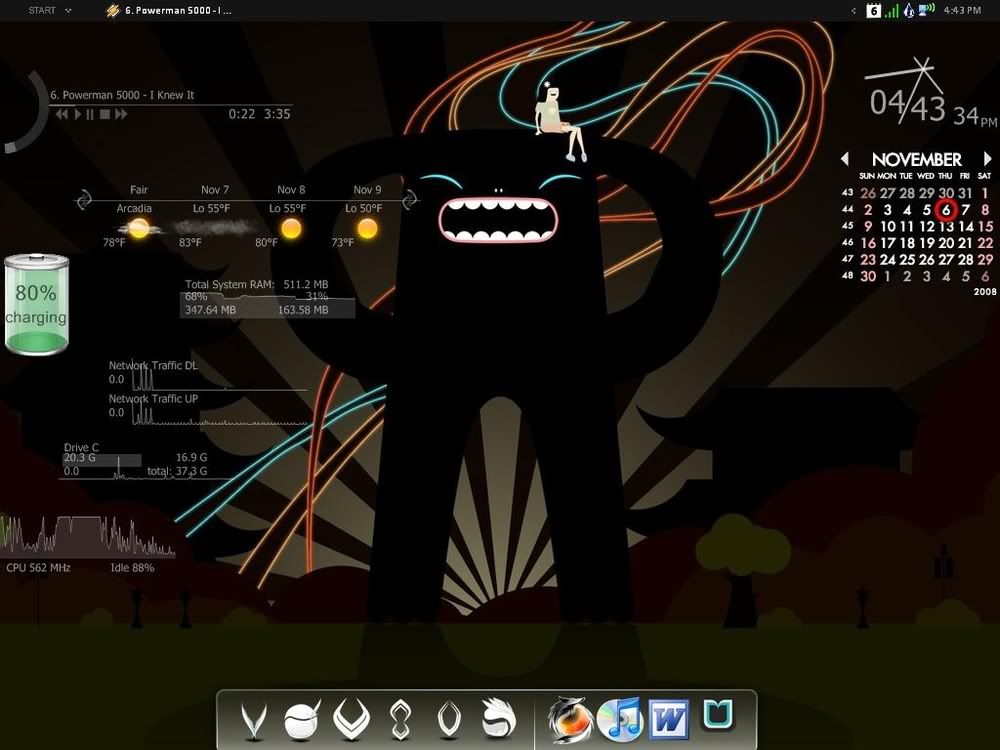
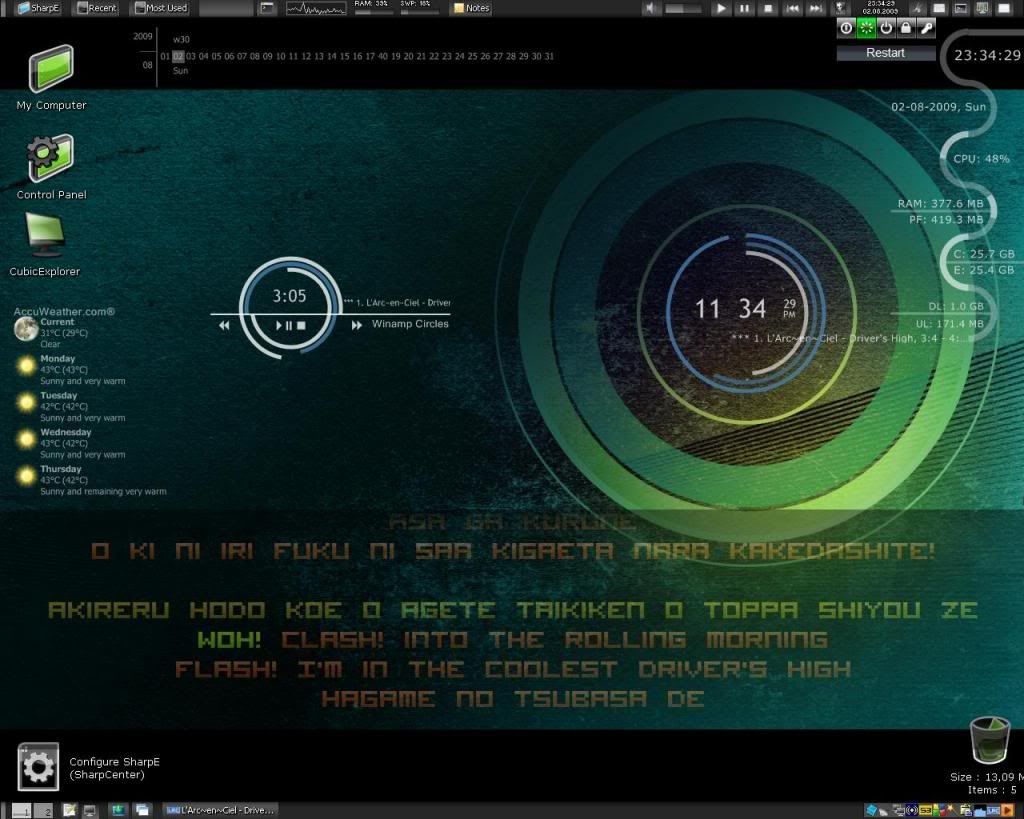
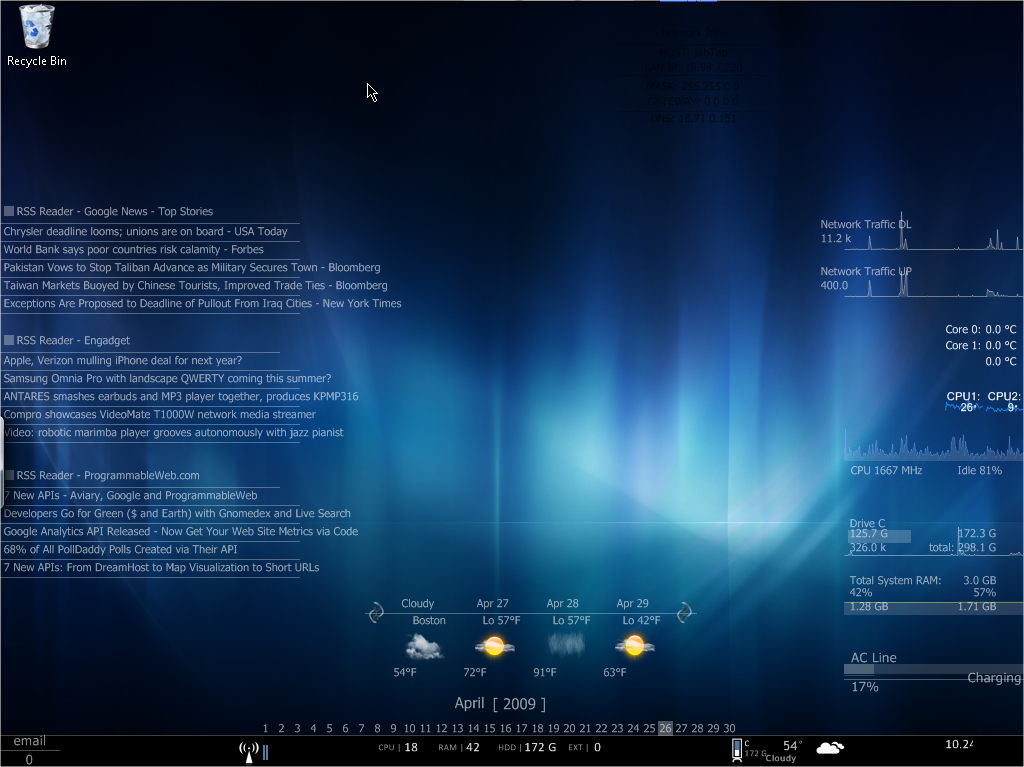
Rainmeter
Ever get tired of the normal computer look? Do you want your operating system to look like something out of a movie, and impress your friends and family? Well, with this tool, you're halfway there!
Rainmeter is a customizable tool that puts many useful and amazing looking tools on your desktop in the form of "Skins". It can be customized virtually any way you want, so long as you have the time to set it up [and learn how to use it if it is your first time]. You can set up clocks, weather, media player information, launcher buttons for your programs, system & network performance monitors, and many more useful tools! The default skins that come with it alone are impressive, but you can also design your own if you are decently skilled at programming. If you aren't, then there are tons of user created skins on the net for this amazing software! The possibilities are endless.
Here are a few screenshots of what Rain Meter looks like, and some different skins that are out there.
[The names they are labeled are not the skin names, simply the name given to the examples. I did not personally make any of these layouts, I simply discovered them for the purpose of showing what this software is capable of.]
Tron Light Cycle [Custom Skin]
Cat
Adventure Time
L'Arc~En~Ciel Themed
Blue [This is one of the most basic skins that comes with the software, so you could easily set up something to this effect]
If you are having difficulty getting the hang of setting up the program, and would like a basic walk-through on how to set it up, change skins, etc, feel free to leave a comment on this post, and one will be posted here [or you can check on the site as well for more in-depth explanations].
Instant Messaging
Pidgin
Pidgin, originally an open source freeware program designed for Linux based Operating Systems such as Ubuntu, has become much bigger, expanding to Windows as well. Pidgin is particularly special, because it allows you to sign into all of your Instant Messengers [AIM, Yahoo, Windows Live, GTalk, etc.] on one client. It uses less system resources then almost every instant messaging client out there, and saves you the hassle of having to log into and have multiple messengers running.
Video Playback
KMPlayer
KMPlayer is a video, audio, and even image playback program that supports virtually every codec and file-type you can imagine; even a few you couldn't. It is one of the least system heavy players out there, and has excellent playback quality, also allowing you to change contrast, brightness, flip the video, resize it, and do just about anything you want with the playback.